> Empower BYOD (Bring Your Own Device) and your mobile workforce
> Enterprise mobile edge management
> Manage roaming users
> Wired and wireless access control
> Mobile device network access
> Centralised access control for the distributed network
|
|
- Identity and context based access control
|
> Integrate with other network mobility solutions
Centralised reference point to track users/client devices, identify rogue devices, plan new deployments, enable rapid troubleshooting of client issues, and visualise RF coverage patterns across the entire mobile infrastructure.
> Manage mobile devices, Macs, PCs, and the entire network from a centralised dashboard.
> Enforce device security policies, deploy software and apps, and perform remote, live troubleshooting.
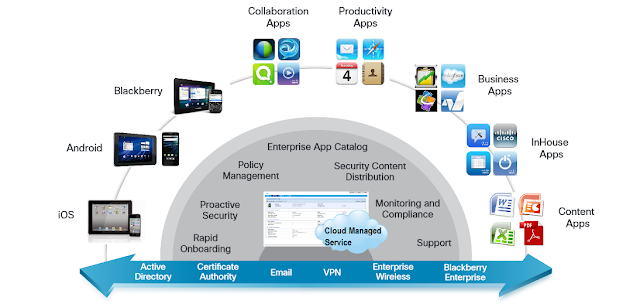
Managed Service
> Full-Lifecycle Managed Mobility
Onboard, secure, manage, monitor, and support mobile devices in your environment while integrating with your existing enterprise systems.
> Streamline mobile collaboration management
- A cloud delivery model enables rapid deployment, flexibility to scale,
and accelerated support for new devices - without initial capital investment.
- A single interface to manage mobile devices, applications, and content
across multiple mobile operating platforms.
- Provides rapid enrollment, bulk provisioning, and over-the-air (OTA)
VPN, Wi-Fi, email, and location policy management of BYOD and
company-provided devices.
|
- Integrations with existing enterprise infrastructure include Microsoft
Active Directory (AD), Certificate Authority, email, VPN, and enterprise wireless
LAN (WLAN).
- Offers centralised reporting, monitoring, and compliance for your
mobile environment.
|
> Rapid onboarding and device enrollment
- Send
enrollment requests using Short Message Service (SMS), email, or a custom
Universal Resource Locator (URL).
- Authenticate
users against Lightweight Directory Access Protocol (LDAP), one-time passcode
(OTP), and two-factor authentication.
|
- Onboard iOS, Android, and BlackBerry mobile devices
- Create
and distribute customised acceptable use policies and End User License
Agreements (EULAs).
- Enroll
corporate and employee-owned BYOD devices.
|
> Device Security
- Define
passcode policies with configurable quality, length, and duration.
- Enforce
encryption and passcode policies.
- Set
device restrictions on features, such as camera, applications, iCloud, and
content ratings.
- Enable
geo-fencing rules to enforce location-related compliance.
|
- Detect
and restrict jail broken and rooted devices.
- Remotely
locate, lock, and wipe lost or stolen devices.
- Selectively
wipe corporate data, leaving personal data intact.
- Define
and implement real-time compliance rules with automated actions.
|
> Central policy management
- Configure
email, calendar, contacts, Wi-Fi, and VPN profiles OTA.
- Approve
or quarantine new mobile devices on the network.
- Create
custom groups for granular or role-based policy management.
|
- Block
collection of personally identifiable information with BYOD privacy settings.
- Decommission
devices by removing corporate data and mobile device management control.
|
> Mitigate security and compliance risks
- Provides
a secure cloud infrastructure with SOC II Type 2, EU Safe Harbor, and FISMA
cloud security certifications.
- Administer
and enforce passwords, encryption, and lock down security.
|
- Remotely
locate, lock, and wipe corporate data on lost or stolen mobile devices.
- Implement
mobile applications and content security policies.
|
> Enhance experience and promote next wave of productivity
- Proactively
push security policies, configuration information, and critical applications
to reduce the end user’s provisioning burden to get started.
- Create,
manage, and distribute public and in-house developed mobile applications
using the role-based application catalogue to view, install, and receive
updates.
|
- Distribute
critical documents and multimedia content to mobile devices - anytime,
anywhere.
- Reduce
support-related downtime with an end-user self-service portal.
|