Sandbox / Threat Emulation
Advanced Threat Protection (ATP)
> Fighting advanced threats
> Complete visibility into network activity including virtualised and encrypted traffic
> Trusted by thousands of enterprises and government agencies worldwide
> Attack emulation
> Test your network defences
> Assess performance and security between private and cloud networks from anywhere in the world
Introduction
- Relying on signature based security systems only protect against known threats and not against zero-day vulnerabilities,
- Heuristic / behaviour based IPS systems have in the past caused organisations a lot of head ache produced by returning too many false positives,
- or replying on big central event and information alert systems is not enough and often is little to late.
The solution is to enlist either a dedicated or integrated sandbox and threat emulation technology to enable to you to inspect and determine the exact payload or intention of a string of actions or executable file.
We also classify security and network testing solutions as ‘threat emulation’ because you should periodically test your systems and configurations against all the possible failure / attack vectors to your network (wired, wireless, applications, users, software, hardware, virtualisation, operating systems, storage, carrier networks, web facing services / the internet). This also helps verify and satisfy compliance and management on future proofing service availability and performance.
To be sure, employ file analyse and threat emulation technology
In recent years 'cyber criminals' have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
These attacks are crafted to evade security tools, such as firewalls, intrusion prevention systems and antivirus gateways.
Advanced threat attacks include spear-phishing, impersonation and polymorphic malware. If not a big brute force attack are more likely to be low-profile, targeted and stealthy to avoid notice and suspicion. These threats are a combination of malware - executable code running on the attack target – and exploits for vulnerabilities, weaknesses on a system, exploiting zero-day vulnerabilities in systems, software flaws to which there is no patch, update or fix or human error in configuration or response times.
Combat threat evasion
- Detect triggers
- Bypass stalling code
Flexible hosted and on-premise solution options
If your Enterprise is restricted by strict privacy laws and policies, deploy on-premise and install components in your data centre.
Alternatively, choose the hosted deployment model and security specialists will manage the backend infrastructure for you.
Sandboxing and Threat Emulation

Sandboxing works by running code inside a tightly controlled environment, in which one can monitor and analyse the code's behaviour.
The sandbox is a blackbox appliance or cloud service that does not touch your network, but is made up of a virtual environment that simulates real-world computing environments, like operating systems, servers, endpoint devices, applications. The sandbox executes the suspicious / malicious code / content to determine the intent of the payload / executable code.
Sandbox Solution Features
> Identify communications by compromised devices
Bi-directional deep inspection capabilities, monitor outbound traffic (including SSL) to identify communications by infected machines. This includes interactions with known botnet command and control servers, communications by infected machines using P2P applications to avoid detection, and traffic to suspicious destinations or countries.> Time Bomb Attacks
Tracking malware over a period of hours or days - instead of seconds or minutes - to build more robust malware profiles of targeted threats.Uncover “Time Bomb” attacks that need to be simulated with custom times and dates (such as Shamoon).
> Identify data leak attempts
Scan all Internet-bound traffic (including content encrypted over SSL) to identify sensitive or unauthorised data, including credit cards, SSNs, financial statements, customer information, medical documents, source code, and other intellectual property.
> Mobile Application (App) Protection
The rapid adoption of mobile computing has created an app-centric global marketplace, ushering in new mobile applications that are driving new business models and revenue. As hackers increasingly target both consumers and enterprise mobile apps, app developers and corporate IT departments must quickly plug security gaps and launch strong and agile app protection measures.
Enable runtime protection that helps to ensure that your application behaves as you intended it to – and that no malware is modifying what the application does!
Application protection products are proven, patented, resilient and inserted directly into the application (in its binary form):
- Do not impact the software development lifecycle (SDLC) and core functionality at run-time.
- Require no changes to the source code
- Seamlessly integration into the build process
- Offer Passive Protection (that protects your app while resident on your device) and Active Protection (that protects your app at run-time) built right into your app
- Leverage a vast array of protection techniques: Obfuscation, Encryption, Checksum, Debugger Detection, Authentication, Value Verification, Repair, Standard Reactions, Alerts
- Are tunable so you can establish the level of robustness/ security
Testing for Threat Protection Systems
Optimising and hardening the resiliency of IT infrastructures
Allow organisations to assess network security and resiliency by testing and validating network and security devices with real-world application traffic and attacks.
Known vulnerabilities – 38K+ known security vulnerabilities, organised by type are available. Attacks are updated frequently to stay current with hacker activity.
Attack evasions – attacks are frequently masked by use of packet fragmentation and other sophisticated techniques. Ixia applies evasions to known vulnerability to increase effectiveness testing.
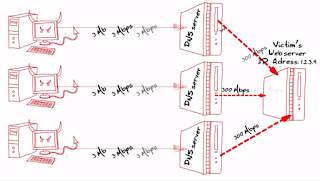
Massive DDoS attacks – simulate distributed denial of service (DDoS) and Botnet attacks to measure cyber infrastructure resiliency. Ixia uses Ixia test ports’ customised logic and scale to mount very large-scale DDoS attacks.
Encryption – IPsec encryption is used in two ways. Encryption with “good” traffic serves to measure VPN gateway throughput. Encryption with “attack” traffictests security effectiveness and accuracy for attacks delivered over secure connections.
Multi-play traffic – sends real-world, stateful traffic to measure security appliance performance. This means that the true, realistic performance, including QoE, of security mechanisms can be measured – not just raw throughput.
Decryption / Unpacking System
Most modern malware is compressed or encrypted to evade traditional file matching systems. This system unveils the actual content for further analysis to detect stealthy polymorphic malware. Think of it as matching the inner components, or true DNA of a virus.
Simulate Attacks
- SSDP amplification / reflection Attacks
- M-SEARCH Requests
> Validate Malware-Protection Effectiveness
Vulnerability patching your servers and endpoints are a very good protection for an enterprise, but it needs to be tested to ensure it fully remediates the vulnerability for attacks.
Signature updates for an intrusion prevention system (IPS) is a solid form of protection, but it needs to be tested to ensure it can detect and block an attack.
High speed Ethernet test solutions were recently used to test and verify the performance of the Cisco Nexus 7718 high density and high scale networking switches.
The transition to 100GbE networking technologies is a necessary component of
today’s global service provider and large enterprise data centers, and the need for high speed Ethernet technologies that can scale and maintain performance against rapidly increasing bandwidth demands is critical.
> Emulate real-world network loads
Test IP forwarding devices such as routers and switches that deliver video, VoIP, data services and business VPNs.
|
|
Cloud-based Sandboxing Services
> Cloud Based Sandbox & File Analysis
The sandbox environment consists of various operating system simulators that execute suspicious programs based on lists of activities and attributes.Security researchers are based around the world, providing 24x7 round-the-clock malware analysis.
Contact us today to discuss your requirements in more detail.

P: +44(0)7714 209927
S: +44(0)1273 329753
|

info@securenetconsulting.co.uk
|