Security researchers have spotted a malware family dubbed RubyMiner that is targeting web servers worldwide in an attempt to exploit their resources to mine Monero cryptocurrency.
RubyMiner, was first spotted last week when a massive campaign targeted web servers worldwide, most of them in the United States, Germany, United Kingdom, Norway, and Sweden.
The experts believe that a single lone attacker is behind the attacks, in just one day he attempted to compromise nearly one-third of networks globally.
“In the last 24 hours, 30% of networks worldwide have experienced compromise attempts by a crypto-miner targeting web servers.” read the analysis from Check Point.
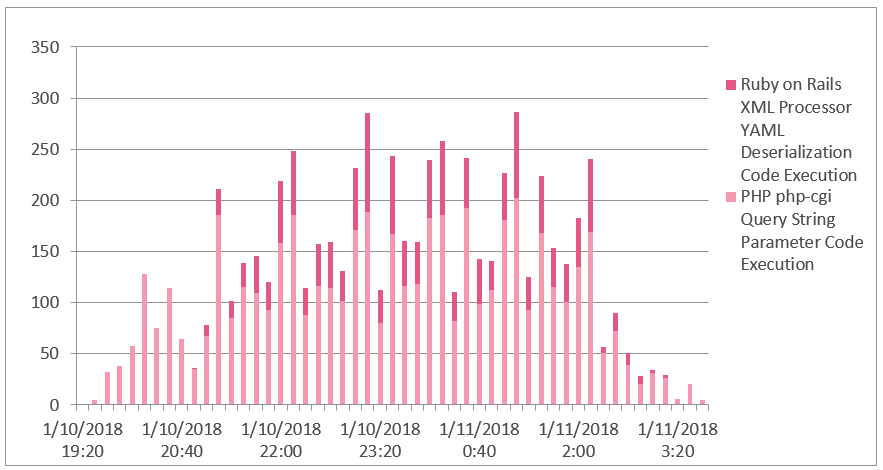
“During that period, the lone attacker attempted to exploit 30% of all networks worldwide to find vulnerable web servers in order to mobilize them to his mining pool. Among the top countries targeted are the United States, Germany, United Kingdom, Norway and Sweden, though no country has gone unscathed.”
Having entered 2018, it seems that actors are again attempting to recruit any available machine for the sole purpose of self-profit. What was previously seen as a minor annoyance has turned into a huge wave of attack attempts across the globe, for it seems attackers are no longer satisfied with just personal computers and are now targeting powerful web servers to increase their computational resources.
With a new attack vector, aiming to install a Monero miner on web servers, the attacker in this case was looking to get more bang for his buck by using the extended computation power of web servers.
Surprisingly, by using old vulnerabilities published and patched in 2012 and 2013, it doesn’t seem that stealth was part of the attacker’s agenda either. Instead, the attacker chose to exploit multiple vulnerabilities in HTTP web servers, to distribute an open source Monero miner – XMRig.
In fact, XMRig usually sends a donation of 5% of the revenue gained from the mining process to the code’s author. However, even this amount was too much for the attacker to part with as that ‘donation element’ was deleted from the code, giving the enthusiast 100% of the profit.
Up to the moment of publication, approximately 700 servers worldwide have been successfully enslaved to this mining pool, making our villain for now only $540 richer…but this is just day one.
Credit: Check Point
