 |
Compliance
Solutions that address industry compliance requirements for data protectionClick below to explore more specific solutions for individual compliance regulations.
> Payment Card Industry Data Security Standard (PCI DSS) > GDPR - European Data Protection Directive (now General Data Protection Regulation (EU 2016/679) > Sarbanes Oxley (SOX) > ISO 27001:2 > HIPAA > Criminal Justice Information Services (CJIS) Security Policy > GCSx / Code of Connection (COCO) 4.1 > Federal Information Security Management Act (FISMA) | > NIST (National Institute of Standards and Technology) > North American Electric Reliability Corporation (NERC) > The Basel Capital Accord (Basel II) > Australian Signals Directorate (ASD) > Japan's Financial Instruments and Exchange Law (J-SOX) > Monetary Authority of Singapore Technology Risk Management Guidelines (MAS-TRMG) > Gramm-Leach-Bliley Act (GLBA) |
> Security Compliance requires evidence of data security and monitoring
> Solutions for Compliance and Risk Professionals
> Prevent targeted attacks and malicious software that evade traditional security methods
> Improve IT systems performance by standardising endpoint configurations
> Audit and report on all software changes to demonstrate compliance
> Lower the cost and uncertainty of compliance audits
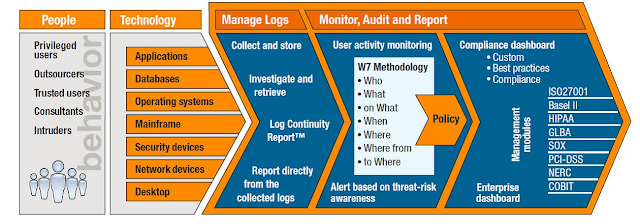
> End-to-end security compliance
> Data Backup, Replication, Mobility, Wireless Security, Testing & Recovery solutions for compliance> Automate Compliance
|
|
> Sensitive Data Discovery
Use Sensitive data discovery to discover and audit all sensitive data within the organisation, in order to prepare the most comprehensive incident-response plan possible.> Privileged Password Management
- Integrate with Microsoft System Centre to Securely Manage Privileged Accounts for GRC Compliance.
- Discover and change all default privileged passwords on each existing, new and changed hardware and software.
- Providing audit trails of all privileged access requests, protected systems and applications.
- Proving that individuals who are terminated or change job roles no longer have access.
- Documenting a need-to-know when it comes to each privileged access.
> Real-Time File Information
Real-time file tracking provides a live inventory of anything that executes on any of your computers, with a full audit trail of what created it, when it was created, what it did, if it deleted or changed itself, and more.
> Healthcare Security and Compliance solution considerations
More healthcare workers than ever before are taking care of patients outside of the hospital; including home care and traveling nurses. With an increasingly mobile workforce, healthcare employees rely on portable devices such as laptops and tablets to access patient information and update healthcare records on the go.
Monitoring Requirements
- network monitoring
- monitor access points
IT Services
Provided by experts with hands-on experience> PCI Assessment (identify gaps in PCI compliance)> Incident Response |
> Computer Forensics> Legal Support |
Training
Enterprise security, law-enforcement, and government professionals in
> Digital Forensics> E-discovery |
> Security Intelligence> Incident Response |
SSAE16, SOC-1, SOC-2, and SOC-3

Statements on Standards for Attestation Engagements (SSAE) 16 Type 2 SOC 1 for service organisations.
An internationally recognised third-party assurance audit that establishes service organisation reporting standards. Type 2 SOC 2, formally known as Reporting on Controls at a Service Organisation Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy.
Also See
- Risk Mitigation- Security Analytics Solutions
- Incident Response
Contact SecureNet Consulting today for solutions advise, professional services, engineering and proof of concept resources for compliance solutions.












